How to Abuse and Fix Authenticated Encryption Without Key Commitment
Authenticated encryption (AE) is used in a wide variety of applications, potentially in settings for which it was not originally …
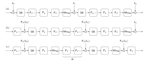
The SPHINCS+ Signature Framework
We introduce SPHINCS+, a stateless hash-based signature framework. SPHINCS+ has significant advantages over the state of the art in …
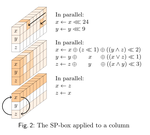
ShiftRows Alternatives for AES-like Ciphers and Optimal Cell Permutations for Midori and Skinny
We study possible alternatives for ShiftRows to be used as cell permutations in AES-like ciphers. As observed during the design process …
Mind the Gap - A Closer Look at the Security of Block Ciphers against Differential Cryptanalysis
Resistance against differential cryptanalysis is an important design criteria for any modern block cipher and most designs rely on …
Finding Integral Distinguishers with Ease
The division property method is a technique to determine integral distinguishers on block ciphers. While the complexity of finding …
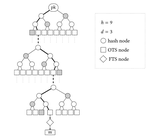
Putting Wings on SPHINCS
SPHINCS is a recently proposed stateless hash-based signature scheme and promising candidate for a post-quantum secure digital …
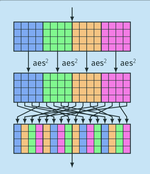
Gimli: a cross-platform permutation
This paper presents Gimli, a 384-bit permutation designed to achieve high security with high performance across a broad range of …
Haraka - Efficient Short-Input Hashing for Post-Quantum Applications
Recently, many efficient cryptographic hash function design strategies have been explored, not least because of the SHA-3 competition. …
Troika: a ternary cryptographic hash function
Linear codes over finite fields are one of the most well-studied areas in coding theory. While codes over finite fields of …
The SKINNY Family of Block Ciphers and its Low-Latency Variant MANTIS
We present a new tweakable block cipher family SKINNY, whose goal is to compete with NSA recent design SIMON in terms of …
A Brief Comparison of Simon and Simeck
Simeck is a new lightweight block cipher design based on combining the design principles of the Simon and Speck block cipher. While the …
State-recovery analysis of Spritz
RC4 suffered from a range of plaintext-recovery attacks using statistical biases, which use substantial, albeit close-to-practical, …
Observations on the SIMON block cipher family
In this paper we analyse the general class of functions underlying the Simon block cipher. In particular, we derive efficiently …
Security of AES with a Secret S-box
How does the security of the AES change when the S-box is replaced by a secret S-box, about which the adversary has no knowledge? Would …
Practical Attacks on AES-like Cryptographic Hash Functions
Despite the great interest in rebound attacks on AES-like hash functions since 2009, we report on a rather generic, albeit …
Differential Cryptanalysis of Keccak Variants
In October 2012, NIST has announced Keccak as the winner of the SHA-3 cryptographic hash function competition. Recently, at CT-RSA …
Practical Attacks on the Maelstrom-0 Compression Function
In this paper we present attacks on the compression function of Maelstrom-0. It is based on the Whirlpool hash function standardized by …